What kinds of anti-counterfeiting measures exist and which one is the best?
Counterfeiting is a pervasive problem that poses significant challenges to businesses and consumers alike. The increase of counterfeit products not only leads to economic losses but also jeopardizes consumer safety and damages brand reputation. To combat this growing menace, various anti-counterfeiting solutions have emerged. In this article, we will explore some of the best anti-counterfeiting solutions currently available and evaluate their effectiveness in protecting authenticity.
1. Unique Identification Technologies
Unique identification technologies provide a means to differentiate genuine products from counterfeits by incorporating distinctive elements into the product or its packaging. These technologies are categorized into logical security, such as unique IDs, and physical security, such as holograms and others. Logical security on a product can be copied, as the protection method is only based on storage of the IDs in a data base. Physical security on the product itself is harder to copy, however in contrast to logical security there is (for most elements) no uniqueness to it.
Common technologies include:
Holographic Security Patterns: Holographic security patterns offer visual authentication effects that are difficult to replicate. They often contain overt, covert, and forensic security features, making them highly reliable anti-counterfeiting tools. However, it is important to note that only holograms with special (patented) security element are truly secure. Standard embossed holograms, which are readily available on the market, are typically intended solely for marketing purposes, as they can be copied.
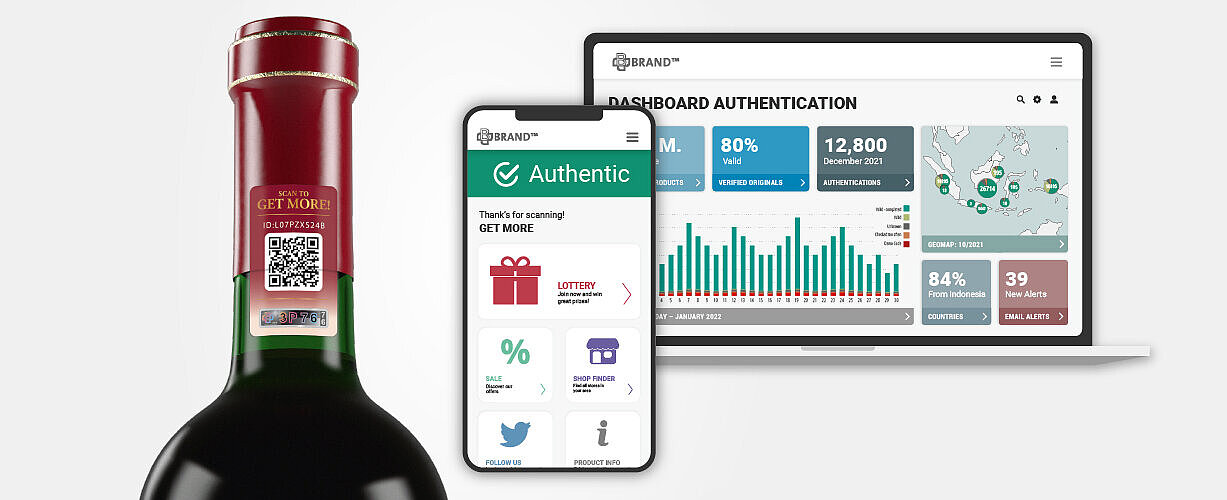
QR codes and Barcodes: QR codes and barcodes enable consumers to verify product authenticity by scanning them, using smartphones or dedicated apps. Authentication data can be securely stored and retrieved from a centralized database or blockchain, providing real-time validation. Without a connection to a database, QR codes are not secure, as they can be copied.
RFID and NFC Tags: Radio-frequency identification (RFID) and near-field communication (NFC) tags allow for secure and automated product tracking and consumer authentication throughout the supply chain. These technologies offer real-time insights into product movement, ensuring authenticity from manufacturing to point of sale. However, one has to be aware that these technologies are:
- More cost-intensive
- Only NFCs can be read by smartphones; RFIDs cannot
- NFCs cannot be used for bulk reading in logistics.
- There are tags with and without copy protection. The fact that a tag is shielded from further modifications or the writing process does not mean it can't be copied.
2. Tamper-Evident Packaging
Tamper-evident packaging solutions provide visible indications of tampering or unauthorized access to a product. They instill confidence in consumers by assuring them that the product has not been compromised. Some notable examples include:
Security Seals: Tamper-evident seals, often with unique identification features, can be applied to packaging or containers to ensure integrity. These seals are specifically engineered to break or leave visible marks upon removal, thereby creating irreversible marks that prevent re-closing without noticing the tamper attempt.
Shrink Wrapping: Heat-shrink film tightly wraps around a product, making it evident if the package has been opened or altered. This cost-effective solution is commonly used for protecting various consumer goods. Please be aware that if they are not combined with other secure anti-counterfeit technologies, they can be copied.
3. Track and Trace Systems
Track and trace systems leverage serialisation and authentication technologies to monitor the movement of products across the supply chain. These systems enable stakeholders to identify and track individual items from production to the point of sale. Key solutions in this category include:
Serialisation Codes: Unique serial numbers or codes are assigned to each product or packaging unit, allowing for traceability and verification throughout the supply chain. Manufacturers, distributors, and retailers can authenticate products using these codes. The security in these systems – most of the time – comes from a very tight tracking that would detect when a copied code is suddenly ‘injected’ into the supply chain at a position where it should not be (as everything is tracked).
Blockchain Technology: Blockchain offers an immutable and transparent ledger that can record product information and transactional data. By storing data in a decentralized manner, it enhances trust and enables easy verification of product provenance. The obstacle at hand is the requirement for a distinct identification feature on the real product to identify the digital twin in the blockchain. The complete blockchain is worthless if the ID or scanning process can be fooled with a copy.
4. Hidden Technologies
Hidden technologies cannot be identified with the naked eye or authenticated by a smartphone without the use of additional tools. These anti-counterfeiting technologies can only be authenticated by experts using a special device, like a UV spotlight.
Notable examples include:
Invisible Ink and UV Markings: Invisible inks and ultraviolet (UV) markings are applied to products or packaging. These features are invisible to the naked eye but become visible under specific lighting or with the use of UV detectors, allowing for easy authentication.
Microtaggants: Microtaggants are microscopic particles (DNA taggants, rare earths) or UV fibers embedded in products, each with a unique signature. These can be authenticated using advanced laboratory equipment, enabling precise verification of product authenticity.
5. Forensic Technologies
Forensic technologies employ specialized features that can only be detected using advanced laboratory equipment or expertise. These solutions provide an additional layer of security against counterfeits. For example, one would employ a chemical analysis to prove authenticity.
What should be the basics of a good anti-counterfeiting technology?
Fact is that there is a world of different anti-counterfeiting solutions on the market and we understand that it can feel a bit overwhelming to choose the right one.
We would like to support your decision-making by giving some tips on what to look out for and how a KURZ SCRIBOS solution fulfills these requirements:
- The best anti-counterfeiting solution is the one that cannot be copied by a counterfeiter
Our KURZ SCRIBOS solutions are developed, patented and produced in-house and therefore cannot be copied by any counterfeiter. They feature a multi-level security combination of overt, covert, and forensic elements to provide multiple layers of protection to your products. All of our levels are serialized and repeat the unique ID (or a part of it) in some form. We have not found a successful copy attempt of our solutions in the 20 years we have been in business.
It is always best to choose an anti-counterfeiting technology that can only be produced and provided by one supplier. If you can buy from several providers, you run the risk that the counterfeiter is also purchasing from these sources.
- The best anti-counterfeiting solution is one that involves the end customer
Our solutions give you the powerful ability to directly involve your customers. To authenticate their product, the customer only has to open his camera on his smartphone, scan the label/marking and is then guided through a one-click authentication process, which is accessible without any app. By scanning, your customers help you find counterfeit hot spots and basically become an army of detectives for your company. Furthermore, digital marketing measures can be integrated after the scanning process, f. ex. you can link to your company website and social media platforms, offer discounts or ask for customer feedback.
As a result, by involving your end customer, you can unlock the full potential of your anti-counterfeiting solution.
- The best anti-counterfeiting solution gives you track and trace abilities
Our solutions can all be connected to our digital platform SCRIBOS 360. Our platform not only helps you detect counterfeit hot spots or grey market activities. It also gives you valuable insights into your market and helps you set up digital marketing campaigns. Each scan is monitored, thereby enabling you to monitor your products and determine their location – globally.
So which solution is the best for me?
As the battle against counterfeiting intensifies, businesses must employ robust anti-counterfeiting solutions to protect their brands and consumers. By leveraging unique identification technologies, tamper-evident packaging, track and trace systems, and hidden technologies, organizations can significantly reduce the risk of counterfeit products entering the market. However, it is important to adopt a multi-layered approach tailored to the specific needs of each industry and product. Ultimately, investing in an anti-counterfeiting solution that in some way involves your customers has been proven to be the most effective way to safeguard the authenticity of your products and maintain trust in the marketplace. Furthermore, it is essential to have a powerful cloud/IT system in place that actually gives you the ability to identify hot spots in real time and take targeted action. The best anti-counterfeiting solution therefore always includes a security feature that is combined with a Cloud/IT system.
We would be delighted to provide assistance to you in identifying the most suitable anti-counterfeiting solution for your requirements, if desired, incorporating powerful extras such as consumer loyalty programs and track & trace capabilities.




